Monday, March 31, 2014
MS Office See Right Through
See Right Through
Ever find yourself trying to create a "cut-out" or frame effect for a PowerPoint slide? (One shape inside another with the inside shape "see thru" to the slides background).
Maybe something like this?

If this is something youve wished you could do then Ive got good news for you - you can and its easier than you may have every imagined.
Obviously, the first step is to create the shapes youre going to use for your cutout.
Since its the inside shape were looking to make into the cut-out its the one we must direct out attention to.
To create this "see thru" effect we simply need to set the shapes fill to the background fill. Fortunately, this doesnt mean trying to match colors or search out patterns… we simply tell PowerPoint to use the background and it will.
So, heres where we find the setting for background fill.
Older versions of PowerPoint:
Right-click on the shape and choose Format AutoShape.
On the Colors and Lines tab of the Format AutoShape dialog box you need the Fill section.

Click the down arrow to the right of the current fill color.
At the bottom of the list you should find Background… choose it.
Click OK to exit to your presentation.
PowerPoint 2007:
Right-click on the shape and choose Format Shape.
Youll be presented with this Format Shape dialog box. Go to the Fill category (chosen from the list on the left side.)

Choose Slide background fill and click Close to return to your presentation.
And thats it… when you place this shape over another it will appear to be see thru.
Oh… and one more really cool thing… if you move the shape around youll find that the fill will "move" too. It really is a fill of the background behind the shape exactly as the background appears at any given location.
~ April
Did you like this Office Tip? Rate or add to it here:
http://www.worldstart.com/
Sunday, March 30, 2014
Screen o Meter
Screen-o-Meter
I ran into a problem the other day. I needed to know how big an envelope was, but I couldn’t find a tape measure or a ruler to save my life. So, I started looking online for one and ran into this Web site!
Screen-o-Meter is a site that allows you to measure things online with your monitor’s screen. All you need to know is the size of the screen your monitor has. If you were to measure it, you would measure the diagonal length of the screen from corner to corner. The site is set up to work with TFT and LCD monitors, but with some adjustments, you can use it with a CRT monitor as well.
To begin measuring, set the monitor screen size. Choose the correct one from the drop down box on the right hand side of the page.
Next, select how long you want the Screen-o-Meter to be. Then click on the Let’s See button. That will take you to the page where your ruler will load.
On the Measurement page, you can test it to see if its accurate. You’ll put in your screen size and then click on the Check button. When the page loads, there will be a large orange circle. If a CD or DVD fits in the circle perfectly, you know you are calibrated right and youre getting precise measurements.
Back on the main page, under the Main Measurement field, you’ll see a link for a rectangular ruler. Thats how you would measure envelopes and such. You just put in the dimensions you’re trying to get and it makes a ruler for it. For example, you could do 3x5, 5x7, 8x11, etc.
Seeing as I can never find a ruler or tape measure when I need one, I know I’ll be using this Web site a lot. I hope you will too!
http://som_en.showdown.hu/
I ran into a problem the other day. I needed to know how big an envelope was, but I couldn’t find a tape measure or a ruler to save my life. So, I started looking online for one and ran into this Web site!
Screen-o-Meter is a site that allows you to measure things online with your monitor’s screen. All you need to know is the size of the screen your monitor has. If you were to measure it, you would measure the diagonal length of the screen from corner to corner. The site is set up to work with TFT and LCD monitors, but with some adjustments, you can use it with a CRT monitor as well.
To begin measuring, set the monitor screen size. Choose the correct one from the drop down box on the right hand side of the page.
Next, select how long you want the Screen-o-Meter to be. Then click on the Let’s See button. That will take you to the page where your ruler will load.
On the Measurement page, you can test it to see if its accurate. You’ll put in your screen size and then click on the Check button. When the page loads, there will be a large orange circle. If a CD or DVD fits in the circle perfectly, you know you are calibrated right and youre getting precise measurements.
Back on the main page, under the Main Measurement field, you’ll see a link for a rectangular ruler. Thats how you would measure envelopes and such. You just put in the dimensions you’re trying to get and it makes a ruler for it. For example, you could do 3x5, 5x7, 8x11, etc.
Seeing as I can never find a ruler or tape measure when I need one, I know I’ll be using this Web site a lot. I hope you will too!
http://som_en.showdown.hu/
Saturday, March 29, 2014
The Serbian Orthodox Church launches an application prayers for smartphones
The Serbian Orthodox Church (SPC) has launched a free application that allows its followers to access by mobile phone in a booklet of prayers

The Serbian Orthodox Church (SPC), very traditional, remains the fact of technological progress. She announced on its website have launched a free application allowing the faithful to access by mobile phone to a booklet of prayers.
Interested persons, who must have an iPhone or mobile device equipped with the Android can download this booklet Orthodox prayer on the website of the Church (www.spc.rs).
This application was developed with the help of Russian programmers religious and portal www.pravoslavie.ru, Said the Church in a statement posted on its website.
Initially, the prayers will be available in the language called "Church Slavonic", different from Serbian, but understandable to practitioners, told the daily Politika Antonijevic Milos, an IT employee of the diocese of Belgrade.
An overwhelming majority of 7.1 million Serbs are Christian Orthodox. The Church has with them great confidence and great influence.

The Serbian Orthodox Church (SPC), very traditional, remains the fact of technological progress. She announced on its website have launched a free application allowing the faithful to access by mobile phone to a booklet of prayers.
Interested persons, who must have an iPhone or mobile device equipped with the Android can download this booklet Orthodox prayer on the website of the Church (www.spc.rs).
This application was developed with the help of Russian programmers religious and portal www.pravoslavie.ru, Said the Church in a statement posted on its website.
Initially, the prayers will be available in the language called "Church Slavonic", different from Serbian, but understandable to practitioners, told the daily Politika Antonijevic Milos, an IT employee of the diocese of Belgrade.
An overwhelming majority of 7.1 million Serbs are Christian Orthodox. The Church has with them great confidence and great influence.
Monday, March 24, 2014
Identifying The Auto Startup Programs
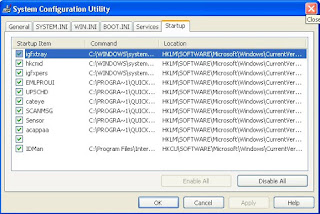
The first step in stopping the auto startup is identifying exactly what is starting up and what its purpose is. To do so, you will use a cool little program called the system configuration utility, which is built into Windows XP, and the Google search engine (www.google.com), which can look up what the entries are for. First, you will need to start up the system configuration utility and write down what programs are listed. To do so, follow these directions:
1. Start up the System Configuration Utility by clicking the Start Menu and selecting Run. Then key in msconfig and click OK.
2. Once the System Configuration Utility has loaded, click the Startup tab.
3. Now that the list of the active startup programs is visible, make a list of all of the items listed with the name as well as the file that is loaded, which is listed under the command column.
4. Once you have your list made, you can start researching which programs should be removed from the list and which programs should stay. Because almost every computer has different programs starting up after logon, I recommend that you browse the Web and look for a specific program and what will happen if it is removed from startup. One interesting site to visit is a database of common startup programs called Answers That Work. It is located at cant present you with recommendations for each of the programs listed. If you can not find one of your programs listed on that site, just do a quick search on Google and most likely you will find several Web sites telling you what that program does and what removing it will do.
Saturday, March 22, 2014
HIDE FULL DRIVE PARTITION
Hide full drive partition.
It is often seen that many people want to secure their data from other users or their friends. For this purpose they use different methods to hide their data but all these tricks are not reliable. BUT now I am telling you a secure method to hide full drive. You can put all your data in a drive and after applying this trick you will be able to hide full drive. To learn this trick, follow these steps.
- First of all logged into administrative account.
- Click on start, open run and type “CMD” and press enter.
- Type “diskpart” and press enter.
- After few seconds diskpart utility will appear.
- Now type “list volume” to show list of volume and press enter.
- Select the Drive or volume that you want to hide. If you have four drives C,D,E,F, and you want to hid “D” drive, then type “select volume 1” and press enter.
- Now in the next step type "remove letter D" to hide this drive.
- Close CMD and open My computer to check…drive D is not there…
- Now if you want to show the hidden drive then in step 7 type “assign drive d” and check “My computer”. Drive is back now.
- Excellent trick, try it now.
 | |
| image (hide system drive) |
Installing Printers and Printer Drivers
(The drivers for the printer were already copied to a folder on the Hard Drive of the PC.)
- Hook up the printer to the computer.
- When the add printer wizard comes up, let it go through the screens until it gets to a dialog asking where to look for the drivers. Check to browse on the Hard Drive and navigate to the folder where the drivers were copied.
- Go through the next screens.
- If the printer drivers installed successfully, there will be a balloon window saying so.
- It should also prompt you to print a test page.
- Print the test page, and then you know that youre good to go.
Read more »
- Hook up the printer to the computer.
- When the add printer wizard comes up, let it go through the screens until it gets to a dialog asking where to look for the drivers. Check to browse on the Hard Drive and navigate to the folder where the drivers were copied.
- Go through the next screens.
- If the printer drivers installed successfully, there will be a balloon window saying so.
- It should also prompt you to print a test page.
- Print the test page, and then you know that youre good to go.
About Me Contact Me Kalpesh Sorthiya
.
.

Hi..im Kalpesh Sorthiya from surat, india. i love Computer, Meditation and other Secret Knowledge. im Computeri Eng. Computer and Internet 5 years Experience and i Write Tipsgo.com to Help other People Computer Repair, Internet, Marketing, online Money and other Secret tips and tricks Share with People.
Add Me
Twitter
Facebook
Google+
MySpace
YouTube
Contact Me ...
kalpesh.sorthiya@gmail.com
.
.
Read more »
.

Hi..im Kalpesh Sorthiya from surat, india. i love Computer, Meditation and other Secret Knowledge. im Computeri Eng. Computer and Internet 5 years Experience and i Write Tipsgo.com to Help other People Computer Repair, Internet, Marketing, online Money and other Secret tips and tricks Share with People.
Add Me
Google+
MySpace
YouTube
Contact Me ...
kalpesh.sorthiya@gmail.com
.
.
Nero 6 3
Nero Edition 6.3
1A23-0009-5030-2246-6907-8435
You can download Nero version 6.3 from OldVersion.coms Nero Page
(Dont register the software if you use this serial number.)
Read more »
1A23-0009-5030-2246-6907-8435
You can download Nero version 6.3 from OldVersion.coms Nero Page
(Dont register the software if you use this serial number.)
Remove MSN Messenger 3 Way
 How to Remove MSN Messenger?
How to Remove MSN Messenger?Follow This Staps:
1rd way:
The following method works in Windows XP Professional, but
has not been tested on a system with SP1 installed. FYI, Ive seen scripts that are
similar to this, but fail miserably, automatically deleting other much-needed
components! Better to do this slow and manually!
1. Exit MSN Messenger by right-clicking the MSN icon in the notification area, and
selecting Exit.
2. Add the following registry entries, both with a DWORD value of 1:
a. HKEY_LOCAL_MACHINESoftwarePoliciesMicrosoftMessengerClientPreventRun
b. HKEY_LOCAL_MACHINESoftwarePoliciesMicrosoftMessengerClientPreventAutoRun
3. Open a command prompt by clicking Start/Run, then typing "command" and clicking OK.
4. Uninstall MSN Messenger by typing "rundll32 advpack.dll,LaunchINFSection %systemRoot%INFmsmsgs.inf,BLC.Remove"
5. Uninstall the leftover installation information file by typing
"rundll32 setupapi,InstallHinfSection BLC.Remove 128 %systemRoot%INFmsmsgs.inf"
6. Allow MSN Messenger to be displayed in the Add/Remove Windows Components dialog
in the future (if it pops up again!)
by typing "notepad.exe %systemRoot%INFsysoc.inf" and deleting the word "hide" from the
line that starts with "msmsgs=".
It MAY be possible to skip to this step directly and perform the uninstallation directly from
the Add/Remove Windows Components dialog, but that method MAY leave unwanted
components and has not been thoroughly tested.
7. Cross your fingers and reboot! You will probably get a message asking you to confirm the
removal of some leftover files. Click OK.
2th way:
There Is a way to uninstall Messenger cleanly. I dont know if these steps apply for Home version.
1. Control PanelAdd Remove Programs click on "add remove windows components" on the left hand side.
In the box that pops up...scroll down to the bottom and highlight "windows messenger" then UNcheck the box.
2. Hit next and let the uninstall complete. (its not a very obvious un-install) When its, done make sure you
to RESTART WINDOWS! (the messenger icon will still be in the tray if you dont!)
3th way
1. First, right click the Messenger icon in the system tray and click Exit.
2. Right click the Start button and click the Explore command to open the Windows Explorer.
3. In the Windows Explorer, expand the Program Files folder on the partition where your operating
system is installed (the partition that holds the WINDOWS directory) and right click the Messenger
folder and select Rename.
4. Rename the folder to MessengerDISABLED and press ENTER to commit the name change.
5. Restart the Computer. No more Windows Messenger
Using WPA for a more secure wireless connection

Wi-Fi Protected Access, or WPA, is a new, improved security standard for wireless connections. WPA has addressed the weaknesses of WEP; it was developed to create a viable alternative to WEP that is more secure than that standard. The fundamentals are the same between the standards, but WPA has improved some of the various mechanisms that plagued WEP. For example, encryption keys are now dynamic and change often automatically. Additionally, the complexity of the encryption key has also been increased to help fight off users who try to derive a key from data that they capture. One of the largest improvements in WPA is the addition of authentication to the wireless connection. Now, users have to have the right encryption settings, as well as a valid username and password, to gain access to the network.
This new standard is just starting to gain momentum. Microsoft has released a special patch for Windows XP that adds this new standard to Windows. However, installing the patch will not allow you to use this new standard. Just as with WEP, WPA is programmed into the firmware of the hardware components. In order to use WPA, you must have hardware that specifically supports it. Currently, only a few companies offer base stations and wireless adapters that support this new method of security. However, that will change in time.
The next time you are considering purchasing a wireless base station and adapter, do some research and pick one that supports WPA to ensure that your wireless communications will not be decrypted and your privacy is secure.
Basic Information of Clearing a Printer
Clears which may be harmful to some printer’s parts.
To clean the inside of the printers, open it up and removes all paper. Removes the toner cartridge, or ribbon as your owners manual directs. Use a lint-free cloth or swabs to gently remove built-up dust and dirt.
Do not use a wet cloth, and never spray any kind of liquid cleaner into your printer unless the manufactures recommends doing so.
If the printers have a great deal of dust built up inside, you can use a vacuum cleaner with a narrow nozzle to pull out the dust. If dust appears to be stuck or is embedded in tiny spaces use a can of compressed air to blast it loose, then vacuum it out.
Thanks
How to convert DVDs to AVI or MPEG video files
WikiHow page on steps for converting a DVD to an AVI file or MPEG file.
AutoGK or DVDx can be used.
AutoGK (Official) Tutorial
For Macs
Handbrake, theres also Instant Handbrake.
Handbrake gives a good interface and multiple format/compression options.
Read more »
AutoGK or DVDx can be used.
AutoGK (Official) Tutorial
For Macs
Handbrake, theres also Instant Handbrake.
Handbrake gives a good interface and multiple format/compression options.
Easy To create Free Online TV Channels !
Bangladesh has got slow internet speed.Everybody know that currently series of internet speed provided of WiMax.If you want than you owner create Online TV channels!
 You can easily create Online TV Channels .At first you go to World-TV Web site. After a while to load into the page, and you got see the video and image to link your channels and click the next button.
You can easily create Online TV Channels .At first you go to World-TV Web site. After a while to load into the page, and you got see the video and image to link your channels and click the next button.
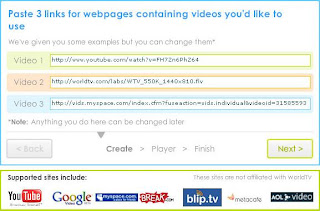 Than next step is the choice of a name for your channels.If you do not have a channels than try another.Than you click next button and select the next button and select the TV channels logo and your email address .
Than next step is the choice of a name for your channels.If you do not have a channels than try another.Than you click next button and select the next button and select the TV channels logo and your email address .
Than ,click next,go to edit page and correct the setting.Add your web site and just above the tab editor for assistance .
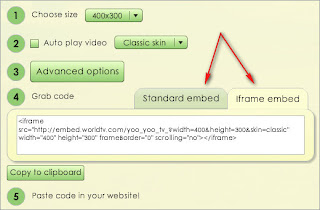 Standard or choose of the embedded or iFrame and you can add your site.
Standard or choose of the embedded or iFrame and you can add your site.
Last you can visit Online channels and watch the TV and video and image .As you can see and thanks for everyone.


Than ,click next,go to edit page and correct the setting.Add your web site and just above the tab editor for assistance .

Last you can visit Online channels and watch the TV and video and image .As you can see and thanks for everyone.
The Computer Restart Cause of a Sudden
Everybody does not love to use the computer.Small and large the computer uses various reasons.99.9 percent people who love there computer.But sometimes unfortunate the computer that behavior it becomes really cincrate with us.Restart not a significant factor in a computer.This is basically due to the difference.
why the computer restart is given below :

1.Internet temperature is one of the main reasons for this.
2.Ram got reason the computer restart.
3. Bad sectors as well as read data from the hard drive and restart the computer hangs when trying to be.
4. USB device connected to the computer when the computer is restarted.
5. Due to the variety of operating systems, operating system crash can not be turned on and start a new try. The operating system is a complex problem, but it can be restarted.
If the hardware is not connected properly, or if you have problems or if you reboot the computer can be connected loss.
6. The virus can also reboot the computer. It is important to use a good antivir.
Its a computer expert to go with your computer.
why the computer restart is given below :
1.Internet temperature is one of the main reasons for this.
2.Ram got reason the computer restart.
3. Bad sectors as well as read data from the hard drive and restart the computer hangs when trying to be.
4. USB device connected to the computer when the computer is restarted.
5. Due to the variety of operating systems, operating system crash can not be turned on and start a new try. The operating system is a complex problem, but it can be restarted.
If the hardware is not connected properly, or if you have problems or if you reboot the computer can be connected loss.
6. The virus can also reboot the computer. It is important to use a good antivir.
Its a computer expert to go with your computer.
Rename and Assign password guest account

Windows XP includes a guest account that is disabled by default. However, at some time, this account may be enabled by an application. If you have Windows XP Professional, I recommend that you disable this account using the old Windows 2000 Local User and Group application. Just in case it becomes enabled again, I recommend that you rename the guest account and also assign it a password. Follow these steps to disable the guest account:
1. Click the Start button and select Run.
2. Key in lusrmgr.msc and click OK.
3. The Local User and Group application will launch. click on user account and Right-click the Guest username and select Set Password.
4. You will be prompted with a warning screen. Just click Proceed.
5. Type a complex password in both boxes and click OK.
6. The password has now been set. Next, rename the account by right-clicking it and selecting Rename.
7. Type in a new name, such as Disabled, and click Enter to save the changes.
The vulnerable guest account is now less of a problem.
Friday, March 21, 2014
Photoshop Tutorial Match color lighting effect

Photoshop Tutorial - Match color (create lighting effect)
How to Twitter Use Can Boost Your Business in Slow Economy

Does your Business need a boost in this slow Economy? If so, you are not alone! Many small businesses are jumping on the Twitter train hoping to gain some momentum in their business.
Twitter use for business is growing rapidly, and, considering that Twitter has over 50 million users, its not difficult to see why!
Timing is Everything. Twitter has surprised everyone by surpassing all other social media networks in its amazing growth. If your business isnt already using Twitter, dont wait any longer. The Twitter train is leaving the station and you want to be on it...every stop it makes could be more exposure, sales and profits for your business!
Twitter use could be the answer to your problems in that it can actually inject some momentum into your marketing plan without adding a lot of expense to it. Its really as simple as this: take the marketing strategies you currently use, add a great Twitter account, and you will have a marketing plan on steroids.
From there, you may want to make adjustments to your marketing plan to either save money or maximize your budget. Twitter use can definitely boost your business and you can use that momentum to make some changes to keep the sales coming in!
The beauty of using Twitter for business is that you can magnify whatever marketing efforts are already in progress by building a community of interested followers and including them in your efforts. Going viral on Twitter is the most effective and affordable marketing available today! Your tweets being retweeted to even more people, over a longer period of time...thats marketing gold!
Twitter is free and simple enough to use. However, effective Twitter use for business can get more complicated in that you want to build a large community and tweet good, relevant content to them. You want to connect with your followers so that they see the value in your product or service with a 140 character message. Its well worth it, though, and it will pay off.
If you already use Twitter for your business, congratulations and keep building your Twitter following. If you havent joined the fun yet, its not too late...get your Twitter account up and running sooner than later. Get your business in front of this wave while you still have time!
Disabling Remote Desktop connection
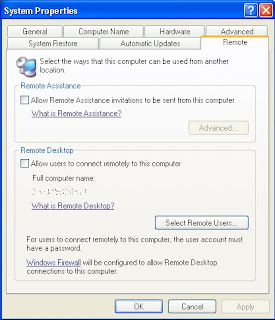
The Remote Desktop feature of Windows XP is a great way to be able to access your
computer when you are away from the office or home. However, if you have poor computer security, the Remote Desktop also is a great way for anyone to be able to access and control your whole computer. Remote Desktop is a very risky application to leave exposed to the world. Its security relies solely on your account password, which for most users is easy to guess.
If you do not use Remote Desktop, then it would be a good idea to disable the feature. Doing so is a snap. Just follow these steps to turn it off:
1. Right-click the My Computer icon on the desktop or in the Start Menu and select
Properties.
2. Click the Remote tab to expose the remote access settings.
3. Next, uncheck the box under Remote Assistance.
4. Uncheck the box under Remote Desktop as well.
5. Click OK to save your changes.
When Remote Desktop connections are disabled, you have one less thing to worry about namely, someone having the ability to break into your computer.
Linux Commands
Most Used Commands for Linux (Servers)
ls
cd
cp (copies files)
mv (rename or move files)
rm (removes--deletes files)
chmod (changes permissions)
Explanation of essential and most used Linux commands
Explanation of Linux (Unix) Commands
ls -l this will list a directory and details about all the listed files
cd .. will go up a directory
cd will change to the highest level directory (root directory)
Read more »
ls
cd
cp (copies files)
mv (rename or move files)
rm (removes--deletes files)
chmod (changes permissions)
Explanation of essential and most used Linux commands
Explanation of Linux (Unix) Commands
ls -l this will list a directory and details about all the listed files
cd .. will go up a directory
cd will change to the highest level directory (root directory)
Easy To Stop Hang With Your Program
How do work ?
At first take my kind regards. Now i share the new post . some problems due to the post being late. Visit our blog to learn something new for a few days before Kidding, I really thought I was parei I would share it. We calai when the computer hangs when it was found that there was a program. The problem here is we want to help in the task manager. So today Ill share the tips with a capei which allows one to be able to hang out with your program.
Lets see it, then right click on the desktop and on the new shortcut, select the shortcuts location, you ask. Copy and paste the following and click Next.
taskkill.exe / f / fi "status eq not responding"
Update My Computer
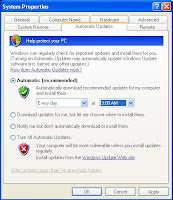
How to Updating your computer?
What are updates?
Microsoft offers important updates, which include security and other critical updates, to help protect your computer against new viruses and other security threats that can spread over the Internet or a network. Other updates contain enhancements, such as upgrades and tools that can help your computer run more smoothly.
Update your Computer Follow This Steps:
1. Click Start, and then click Control Panel.
2. Depending on which Control Panel view you use, Classic or Category, do one of the following:
Click System, and then click the Automatic Updates tab.
Click Automatic (recommended) Option and select the day and time you want Windows to install updates. (Your Select Time Every Day 3:00 AM. Your Computer Update Every Day 3:00 AM)
Click Apply -> OK.
Online Freelancing
What is Freelancing?
A Simply being Freelancing, person an organization with a long-term contract without work. Freelancing a job, depending on the type of freedom.
Freelance Marketplace:
What are the most popular website in the scope of the outsourcing., And at all sites of the freelance marketplace. Freelance marketplace are two types of users and the websites of those who submitted their work for the buyer or the Client and those who do are called Freelancer, provider, seller, or in some cases Coder.
Bid now? To complete the work for a several Freelancing application, called the bid. Bid how much money you will need when / how many days can you be so ullekhy.
...
This should be selected Freelancer: The phrilyansarera klayeta whom he may select from within. Prior work experience, amount of money, and when phrilyarera comments bids based on the klayeta as a Freelancer.
Escrow (Escrow) What? Klayeta successfully perform a task after the completion of the work submitted to the Escrow account named. Was fully completed after the successful Freelancer her understand the payment from the Escrow. The complete service for a specific part (10% or 15%) of the sites is a fee or commission.
Descriptions of Elances :
 Elance is one of the largest online freelance marketplace. Currently working on the best available and are much more amount of money. Again the agreement is based, or hours of work. The number of people in work in elance. There are many reasons for the subscription fee is applied. But all well-known and duniyajure Freelancing Company elance at work.
Elance is one of the largest online freelance marketplace. Currently working on the best available and are much more amount of money. Again the agreement is based, or hours of work. The number of people in work in elance. There are many reasons for the subscription fee is applied. But all well-known and duniyajure Freelancing Company elance at work.
It does not kill us banladesirao. Bangladeshis location at approximately 4 elance number (India, ukreina, Pakistan, Bangladesh). elance at the facility are all larger than it is ESCROW System. It is a system, where the client and the provider, a secure payment system, the two pakserai. Here is the first system in this country, and work with the client at the end of the discount. However, due to problems with any party if the appeal can be made at elance, the elance check all messages - Audit of the party with the best of them....
A Simply being Freelancing, person an organization with a long-term contract without work. Freelancing a job, depending on the type of freedom.
Freelance Marketplace:
What are the most popular website in the scope of the outsourcing., And at all sites of the freelance marketplace. Freelance marketplace are two types of users and the websites of those who submitted their work for the buyer or the Client and those who do are called Freelancer, provider, seller, or in some cases Coder.
Bid now? To complete the work for a several Freelancing application, called the bid. Bid how much money you will need when / how many days can you be so ullekhy.
...
This should be selected Freelancer: The phrilyansarera klayeta whom he may select from within. Prior work experience, amount of money, and when phrilyarera comments bids based on the klayeta as a Freelancer.
Escrow (Escrow) What? Klayeta successfully perform a task after the completion of the work submitted to the Escrow account named. Was fully completed after the successful Freelancer her understand the payment from the Escrow. The complete service for a specific part (10% or 15%) of the sites is a fee or commission.
Descriptions of Elances :
It does not kill us banladesirao. Bangladeshis location at approximately 4 elance number (India, ukreina, Pakistan, Bangladesh). elance at the facility are all larger than it is ESCROW System. It is a system, where the client and the provider, a secure payment system, the two pakserai. Here is the first system in this country, and work with the client at the end of the discount. However, due to problems with any party if the appeal can be made at elance, the elance check all messages - Audit of the party with the best of them....
How to Block or Remove Blogspot Follower User
How to Block or Remove Blogger Follower User?
How to Add Friend Blogapot Follower User?
Some Blogspot follower user use Adult and sexy image. If you are having blogger blog, you will have followers widget for every blog by default. In this case any visitor can become your follower. Now if you wanted to moderate it and blog any follower here are some simple steps to do this. Or else if you wish to Add the follower as friend then also check the below 8 steps.
1. Login to blogger.com.
2. Here, for every blog of you an see followers link if it has minimum one, as you can see in bellow image my blog has 101 Followers
3. Click on Followers Link for the blog for which you want to block some follower
 4. It will show list of followers as shown in bellow image.
4. It will show list of followers as shown in bellow image.
5. Now click on the picture of the follower which you wanted to block
 6. This will show updates and links of follower as well as link for blocking the follower.
6. This will show updates and links of follower as well as link for blocking the follower.
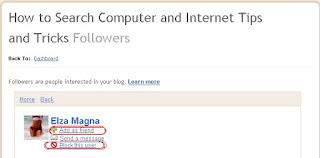
7. Click on Block This User Link and follow the steps and the follower gets blocked from following your blog.
8. If you dont want block the follower but add as a friend then click on Add as friend as shown in the above image.
Thank you....
Read more »

How to Add Friend Blogapot Follower User?
Some Blogspot follower user use Adult and sexy image. If you are having blogger blog, you will have followers widget for every blog by default. In this case any visitor can become your follower. Now if you wanted to moderate it and blog any follower here are some simple steps to do this. Or else if you wish to Add the follower as friend then also check the below 8 steps.
1. Login to blogger.com.
2. Here, for every blog of you an see followers link if it has minimum one, as you can see in bellow image my blog has 101 Followers
3. Click on Followers Link for the blog for which you want to block some follower
 4. It will show list of followers as shown in bellow image.
4. It will show list of followers as shown in bellow image.5. Now click on the picture of the follower which you wanted to block
 6. This will show updates and links of follower as well as link for blocking the follower.
6. This will show updates and links of follower as well as link for blocking the follower.
7. Click on Block This User Link and follow the steps and the follower gets blocked from following your blog.
8. If you dont want block the follower but add as a friend then click on Add as friend as shown in the above image.
Thank you....
Top 10 keyboard shortcuts everyone should know
Using keyboard shortcuts can greatly increase your productivity, reduce repetitive strain, and help keep you focused. For example, highlighting text with the keyboard and pressing Ctrl + C is much faster than taking your hand from the keyboard, highlighting the text using the mouse, clicking copy from the file menu, and then putting your hand back in place on the keyboard. Below are our top 10 keyboard shortcuts we recommend everyone memorize and use.
Ctrl + C or Ctrl + Insert
Copy the highlighted text or selected item.
Ctrl + V or Shift + Insert
Paste the text or object thats in the clipboard.
Ctrl + Z and Ctrl + Y
Undo any change. For example, if you cut text, pressing this will undo it. This can also often be pressed multiple times to undo multiple changes. Pressing Ctrl + Y would redo the undo.
Ctrl + F
Open the Find in any program. This includes your Internet browser to find text on the current page.
Alt + Tab or Alt + Esc
Quickly switch between open programs moving forward.
Tip: Press Ctrl + Tab to switch between tabs in a program.
Tip: Adding the Shift key to Alt + Tab or Ctrl + Tab will move backwards. For example, if you are pressing Alt + Tab and pass the program you want to switch to, press Alt + Shift + Tab to move backwards to that program.
Tip: Windows Vista and 7 users can also press the Windows Key + Tab to switch through open programs in a full screenshot of the Window.
Ctrl + Back space and Ctrl + Left or Right arrow
Pressing Ctrl + Backspace will delete a full word at a time instead of a single character.
Holding down the Ctrl key while pressing the left or right arrow will move the cursor one word at a time instead of one character at a time. If you wanted to highlight one word at a time you can hold down Ctrl + Shift and then press the left or right arrow key to move one word at a time in that direction while highlighting each word.
Ctrl + S
While working on a document or other file in almost every program pressing Ctrl + S will save that file. This shortcut key should be used frequently anytime youre working on anything important.
Ctrl + Home or Ctrl + End
Move the cursor to the beginning or end of a document.
Ctrl + P
Print the page being viewed. For example, the document in Microsoft Word or the web page in your Internet browser.
Page Up, Space bar, and Page Down
Pressing either the page up or page down key will move that page one page at a time in that direction. When browsing the Internet pressing the space bar will also move the page down one page at a time. If you press Shift and the Space bar the page will go up a page at a time
Sharp 85 inch 8k glassse free 3D TV
Early reports from CES 2014 showed that this year might be the year of the humongously big TV with Samsung and Vizio both unveiling TV’s topping the 100-inch milestone. Of course, both TV’s feature the newest 4k technology, allowing one to view TV as one has never viewed it before.
That was until Sharp revealed their designs for an 85-inch, 8k television during their CES press conference. This is not the first time Sharp has unveiled an 85-inch 8k television, doing so during last years CES. The difference this year, however, is that the model is now less of a prototype / more of a reality, and it offers glasses-free, 3D viewing.
Sharp produced the 85-inch TV alongside Phillips and Dolby. The 8k rating for the TV means that it will be able to handle resolutions measuring 7680 x 4320, which is 16 times more than current, standard HD TV’s. (1080p resolutions being 1920 x 1080.)
 That being said, the 85-inch 8k offering from Sharp may be stretching a bit beyond current technological carrying capacity. Much debate has been raised over the past few years concerning whether or not the eye can discern the differences between ultra-high resolutions. Most television producers are currently focusing on furthering the development of 4k resolution televisions (3840 x 2160), a viewing quality which already faces difficulties due to the lack of channel support (due to inadequate technology) from satellite or cable companies.
That being said, the 85-inch 8k offering from Sharp may be stretching a bit beyond current technological carrying capacity. Much debate has been raised over the past few years concerning whether or not the eye can discern the differences between ultra-high resolutions. Most television producers are currently focusing on furthering the development of 4k resolution televisions (3840 x 2160), a viewing quality which already faces difficulties due to the lack of channel support (due to inadequate technology) from satellite or cable companies.
As it currently stands, most experts agree that one could only notice the increase in viewing quality with an 8k TV if one views it at uncomfortably close distances. If that is the case, the one positive aspect of this offering from Sharp would be the glasses-free (autostereoscopic) 3D viewing capabilities.
 Fortunately for Sharp, the company has not placed all of its eggs into one basket. During CES 2014, the company also unveiled new products in its Aquos line, the most impressive of which being the Aquos Quattron Plus, a television offering 10 million more subpixels than standard HD televisions. These extra subpixels places the Aquos Quattron Plus at the level between standard HD and 4k, making it a viable viewing option for those with less-deep pockets and being more compatible with current cable and satellite provider technologies.
Fortunately for Sharp, the company has not placed all of its eggs into one basket. During CES 2014, the company also unveiled new products in its Aquos line, the most impressive of which being the Aquos Quattron Plus, a television offering 10 million more subpixels than standard HD televisions. These extra subpixels places the Aquos Quattron Plus at the level between standard HD and 4k, making it a viable viewing option for those with less-deep pockets and being more compatible with current cable and satellite provider technologies.
Sharp showed some scenes from the Oscar winning movie "Life of Pi" and "Frozen". Good Luck Sharp.
That was until Sharp revealed their designs for an 85-inch, 8k television during their CES press conference. This is not the first time Sharp has unveiled an 85-inch 8k television, doing so during last years CES. The difference this year, however, is that the model is now less of a prototype / more of a reality, and it offers glasses-free, 3D viewing.
Sharp produced the 85-inch TV alongside Phillips and Dolby. The 8k rating for the TV means that it will be able to handle resolutions measuring 7680 x 4320, which is 16 times more than current, standard HD TV’s. (1080p resolutions being 1920 x 1080.)
 That being said, the 85-inch 8k offering from Sharp may be stretching a bit beyond current technological carrying capacity. Much debate has been raised over the past few years concerning whether or not the eye can discern the differences between ultra-high resolutions. Most television producers are currently focusing on furthering the development of 4k resolution televisions (3840 x 2160), a viewing quality which already faces difficulties due to the lack of channel support (due to inadequate technology) from satellite or cable companies.
That being said, the 85-inch 8k offering from Sharp may be stretching a bit beyond current technological carrying capacity. Much debate has been raised over the past few years concerning whether or not the eye can discern the differences between ultra-high resolutions. Most television producers are currently focusing on furthering the development of 4k resolution televisions (3840 x 2160), a viewing quality which already faces difficulties due to the lack of channel support (due to inadequate technology) from satellite or cable companies. As it currently stands, most experts agree that one could only notice the increase in viewing quality with an 8k TV if one views it at uncomfortably close distances. If that is the case, the one positive aspect of this offering from Sharp would be the glasses-free (autostereoscopic) 3D viewing capabilities.

Sharp showed some scenes from the Oscar winning movie "Life of Pi" and "Frozen". Good Luck Sharp.
Thursday, March 20, 2014
Overclockers Titan 400i Dagger PC Story

This laptop was provided to United States as a base laptop system with a spread of internal and external upgrade choices, contact the manufacturer to urge the precise specification you need
Even before you add any upgrades, the Overclockers Titan 400i Dagger prices a reasonably significant £710, therefore is not in rivalry for our Budget obtain award. However, it is a powerful system that stands out among most anonymous laptop black boxes due to its notably snazzy-looking white case. similarly as well-to-do, its well finished and provides you lots of house to figure in.
The laptop is additionally uncommon therein its a water-cooling system for its processor. This makes a high-pitched whine, and therefore the the} case also has fairly lowest soundproofing due to its copious air vents, that ar designed to create it simple to suit additional fans if you wish them. This makes the Dagger aloof from the quietest system we have seen, therefore wed positively suggest keeping this laptop on the ground.
This cooling system ought to enable the PCs Intel Core i5-4670K processor to be overclocked, though Overclockers hasnt done therefore for you. The powerful processor made associate degree overall score of 109 in our benchmark tests. The MSI Z87-G43 motherboard is fitted with 8GB of one,600MHz RAM, effort house for 2 a lot of modules.
The motherboard additionally has 3 PCI slots, 2 PCI-E x1 slots and 2 PCI-E x16 slots. However, one in every of the x1 slots is blocked by the graphics card higher than it and, like most motherboards, the second x16 slot solely runs at x4 speed. There ar six SATA3 ports and a vacant USB3 header.
The cases front panel has simply 2 USB ports and therefore the usual three.5mm mic and electro-acoustic transducer connectors. At the rear of the motherboard, you will find a PS/2 port for a mouse or keyboard, six USB ports and 2 USB3 ports. There are six three.5mm stereo outputs for seven.1 analogue surround sound.
The graphics card comes with the PCs base specification, and may be a 1GB Nvidia GeForce GTX 650 Ti. Wed have liked to own the choice to upgrade the cardboard, because it does not have the performance that hardcore gamers would possibly hope for. attributable to driver compatibility issues with the graphics card, we have a tendency to werent ready to run our Dirt disagreement check, however we have a tendency to saw a reasonably jerky frame rate of twenty three.9fps in Crysis a pair of at extremist quality and a resolution of one,920x1,080. Drop the standard to Extreme, though, and you may see frame rates hit a nearly-smooth average of twenty nine.9fps.
The laptop is supplied with a DVD-RW drive and a 1TB fixed disk. youll add associate degree SSD for the lowest price of £25. sadly, this can be solely a 60GB SSD, that is therefore little on be of rather lowest use. youll get a 120GB SSD for a really cheap £44, that may be a far better plan.
For £156 youll have a matt twenty three.6in Iiyama Prolite E2481HS monitor, that is concerning the market value for this show. whereas several monitors do not extremely like standardization, the E2481HS is associate degree exception. At default settings, it might show simply eighty nine.4% of the sRGB color gamut, and looked rather washed out. once standardization it might show a wonderful ninety seven of sRGB, and hues looked rather more lifelike. sadly, a standardization tool can set you back around £100 anyway, therefore we have a tendency to would like the monitor might show a lot of correct colors out of the box.
While it is easy to become inundated by selection once given a spread of upgrades to pick from, Overclockers has maybe narrowed the sector a trifle an excessive amount of by solely providing the choice of associate degree SSD upgrade for its Titan 400i Dagger. though the laptop is well created and thoughtfully designed, neither the systems base specification nor its upgrades ar particularly sensible worth. If you are on a budget, we have a tendency to suggest the laptop Specialist time A10 professional Elite, whereas those trying to splash out ar happier with the Chillblast Fusion Kestrel.


Android JellyBean 4 1 Vs iOS 6 User Interface
User Interface
LockscreensWell,most of you people are aware of the main difference between Android and iOS -customization vs ease of use.Well,first of all,when you turn your phone on you go to the lockscreen.Well the lockscreens in both the platforms are very different.In Iphone you get the typical Slide to unlock lockscreen,whereas in case of android jellybean you will be confronted with the drag to unlock lockscreen.However.there is one major difference -in case of iOS you are restricted to the Slide to unlock feature whereas in android you will get a whole bunch of third party lockscreens that you can install,thus enhancing your experience.
Check out Android Lockscreen Alternatives
User Interface
Well after the lockscreen comes the user interface.In iOS 6 you are once again presented with the plain icons.In case of android once again it is all about customization.One thing that I noticed is that folders open faster in jellybean than iOS ,maybe because of project butter.
Notification Area
Well in this case it is almost a tie only a slight edge to android because of more allowance of choices in this area.
Effective Guest Blogging Tips
A post for bloggers with effective guest blogging tips to experience its benefits and to perform well in the blogosphere.

Most of the website owners have started considering guest blogging very seriously as it is an effective marketing technique in the online world. Not only bloggers, even multinational companies have started guest blogging for some valid reasons.
If you are an influential blogger, I am sure that you have already started to guest post on other blogs of your same niche and tasting its benefits.
But if you are a newbie blogger, then you might ask “What is guest blogging?” and “Why should I write guest posts on other blogs?”
Yeah, both are good questions! But before answering to it,let me ask some questions because I always taking care and love to read other blogs :)
Add “Do you” for every question of mine!
Now here is the answer for your very first question:
But be sure that your guest post should not ruin the status of the blog where you are appearing as a guest blogger. It means that you need to submit quality guest posts on other blogs and help those blog owners to get good traffic through your posts.
Hope you are now somewhat clear with “Guest blogging and its benefits”. Am I correct?
I always used to write high quality guest posts for my blogging friends and influential bloggers. Also am feeling virtuous as this is my 13th guest post in my 5 months blogging career.
Ok, let me explain some common myths of guest blogging.
Myth #1. Number of guest posts approved is important than its quality.
Some bloggers performing guest blogging just to build backlinks to their blog. They are showing interest to create more number of guest posts on various blogs and never mind about its quality. It is a bad practice and should be avoided by the bloggers.
Truth: Quality guest posts sounds greater than more no. of guest posts submitted just for link-building.
Myth #2: Blogs should have good PR to submit guest post on other blogs.
Newbie bloggers think that their blog should have high Pagerank to submit their guest post on other blogs. It is not true! My guest posts were accepted in PR4 and PR3 blogs and my blog’s page rank is 0. So, don’t hesitate to guest post on energetic blogs even if you have low or zero page rank.
Truth: Valuable guest posts which are helpful for the visitors are readily accepted in famous blogs.
Myth #3: Taking much effort for guest blogging is waste
I came across few bloggers with the statement “Why should I write long and quality posts just for backlinks and I have alternate ways for it”. No it is really wrong and the bloggers should not expect instant results from guest blogging.
Truth: Guest blogging is only effective if it focused to have long term benefits.

Most of the website owners have started considering guest blogging very seriously as it is an effective marketing technique in the online world. Not only bloggers, even multinational companies have started guest blogging for some valid reasons.
If you are an influential blogger, I am sure that you have already started to guest post on other blogs of your same niche and tasting its benefits.
But if you are a newbie blogger, then you might ask “What is guest blogging?” and “Why should I write guest posts on other blogs?”
Yeah, both are good questions! But before answering to it,let me ask some questions because I always taking care and love to read other blogs :)
Add “Do you” for every question of mine!
- Want to increase credibility among your blog readers?
- Need to have more blog subscribers?
- Prefer the natural promotion for your blog?
- Desire to gain more visibility and traffic to your blog?
- Favor effective link building method?
- Wish to make friendship with fellow and prominent bloggers?
Now here is the answer for your very first question:
What Is Guest Blogging?
"Guest blogging is a strategy of appearing on other same niche blogs with your fresh post as a guest."
But be sure that your guest post should not ruin the status of the blog where you are appearing as a guest blogger. It means that you need to submit quality guest posts on other blogs and help those blog owners to get good traffic through your posts.
Hope you are now somewhat clear with “Guest blogging and its benefits”. Am I correct?
I always used to write high quality guest posts for my blogging friends and influential bloggers. Also am feeling virtuous as this is my 13th guest post in my 5 months blogging career.
Ok, let me explain some common myths of guest blogging.
Guest Blogging Myths
Myth #1. Number of guest posts approved is important than its quality.
Some bloggers performing guest blogging just to build backlinks to their blog. They are showing interest to create more number of guest posts on various blogs and never mind about its quality. It is a bad practice and should be avoided by the bloggers.
Truth: Quality guest posts sounds greater than more no. of guest posts submitted just for link-building.
Myth #2: Blogs should have good PR to submit guest post on other blogs.
Newbie bloggers think that their blog should have high Pagerank to submit their guest post on other blogs. It is not true! My guest posts were accepted in PR4 and PR3 blogs and my blog’s page rank is 0. So, don’t hesitate to guest post on energetic blogs even if you have low or zero page rank.
Truth: Valuable guest posts which are helpful for the visitors are readily accepted in famous blogs.
Myth #3: Taking much effort for guest blogging is waste
I came across few bloggers with the statement “Why should I write long and quality posts just for backlinks and I have alternate ways for it”. No it is really wrong and the bloggers should not expect instant results from guest blogging.
Truth: Guest blogging is only effective if it focused to have long term benefits.
Tips To Get Your Guest Posts Accepted
- Try to impress the blog owners whom you are selected to submit your guest posts with polite approach and explain why you have selected their blog to submit your post.
- You should write guest post for related niches with good PR and high authority blogs, so sure to be thorough with their guidelines of guest posting.
- Follow your unique style in writing to stand out from other guest bloggers.
- It is really exciting to see your name on well performing blogs right? So include a simple and gorgeous Author-bio for your guest post.
- Make efforts to engage the visitors from the beginning of your guest post by offering some fresh or unread data for them.
Subscribe to:
Posts (Atom)